Mobile API security is broken—and it’s costing companies millions.
You’ve built a mobile app. Users love it. Downloads are climbing. Everything’s working great. Then your API gets scraped by a competitor. Or credential-stuffed by bot networks. Or cloned by someone who reverse-engineered your app and is now selling premium features for free.
This is the reality of mobile API security in 2025, and traditional security approaches simply don’t work for mobile applications.
Here’s the uncomfortable truth: mobile API security challenges are fundamentally different from web API security. Traditional API security fails spectacularly for mobile applications.The assumptions that work for web APIs—trusted clients, controlled environments, secure storage—completely fall apart when your code runs on millions of devices you don’t control.
This article is your comprehensive mobile API security framework for building APIs that can actually withstand modern attack vectors. We’ll cover the unique security challenges of mobile-to-backend trust, specific exploitation patterns targeting mobile APIs, architectural approaches to strengthen backend resilience, and practical strategies for multi-platform deployment.
Whether you’re a CTO at a mobile-first company, a backend architect working on mobile infrastructure, or a security engineer responsible for mobile API security, you’ll walk away with actionable strategies to protect your data, endpoints, and monetization logic.
Don’t want to tackle this alone? Mobile API security is complex, and the stakes are high. You can work directly with us at Iterators to secure your mobile infrastructure—schedule a free consultation to discuss your specific security challenges.
Let’s start with why your current API security probably isn’t good enough.
Why Traditional API Security Fails for Mobile Applications
Web APIs and mobile APIs seem similar on the surface. Both use HTTP. Both authenticate users. Both return JSON.
But that’s where the similarities end—and where mobile API security becomes critical.
Mobile API security differs fundamentally from web API security because when you build a web application, the client code runs in your browser, on your infrastructure.
For a comprehensive overview of mobile application security risks, refer to the OWASP Mobile Application Security Verification Standard, which provides detailed security requirements for mobile apps.
The Fundamental Mobile API Security Trust Problem
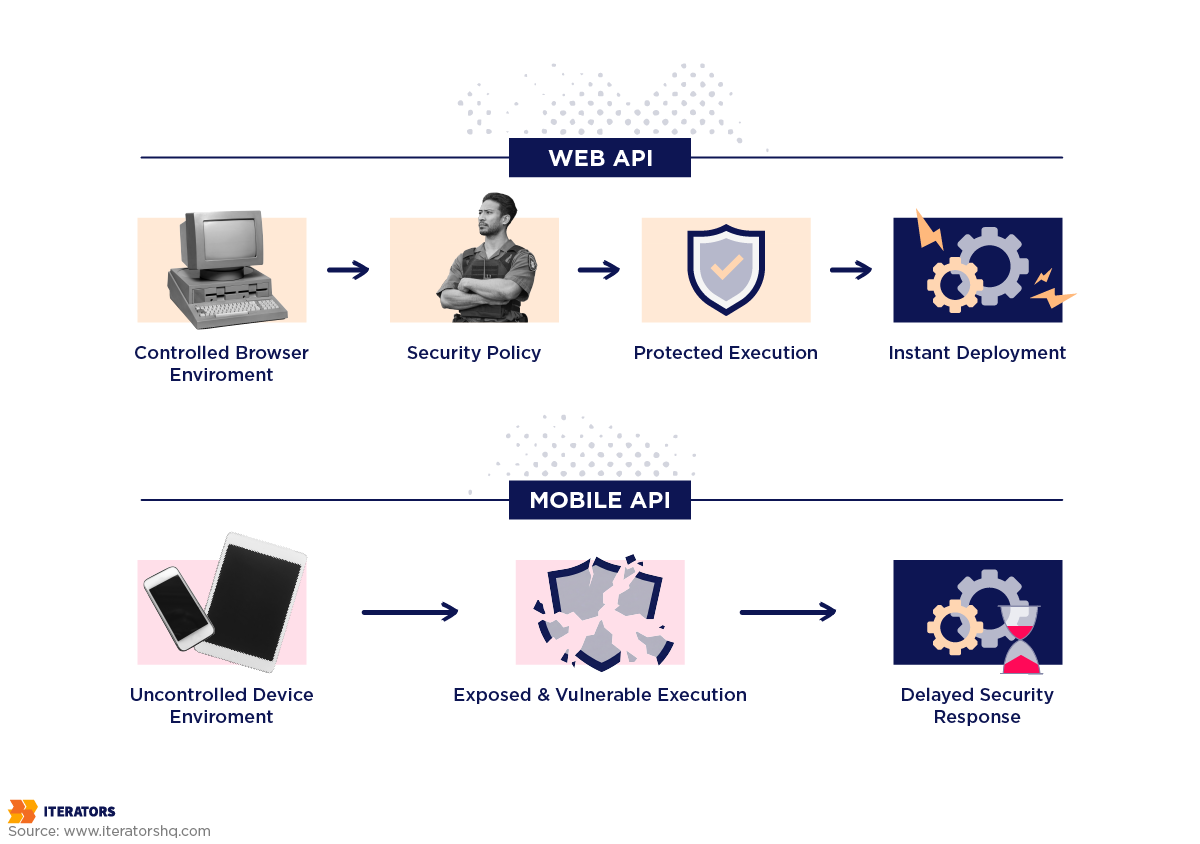
When you build a web application, the client code runs in your browser, on your infrastructure. You control the execution environment. You can enforce security policies. You can update the code instantly.
With mobile apps, you ship executable code to devices you’ll never see, running operating systems you don’t control, on networks you can’t trust. Your security model just collapsed.
The web security model assumes the client is potentially malicious but the environment is controlled. You can’t inject arbitrary JavaScript into a properly configured web app because Content Security Policy blocks it.
The mobile API security model must assume both the client AND the environment are hostile. Anyone with a jailbroken iPhone or rooted Android can modify your app binary, intercept network traffic, and inject arbitrary code.
This creates mobile API security attack surfaces that simply don’t exist in web applications:
Client-side code exposure: Your app binary contains your API endpoints, authentication logic, and business rules. Attackers can reverse-engineer everything.
Device variability: You’re not serving one browser version—you’re supporting dozens of OS versions, manufacturers, and custom ROMs, each with different security capabilities.
Network conditions: Mobile devices constantly switch between WiFi, cellular, and offline states, creating opportunities for man-in-the-middle attacks.
Long-lived installations: While you can deploy web updates instantly, mobile apps might run outdated code for months or years.
The Business Risk Equation
These mobile API security technical differences create real business risks that affect your bottom line:
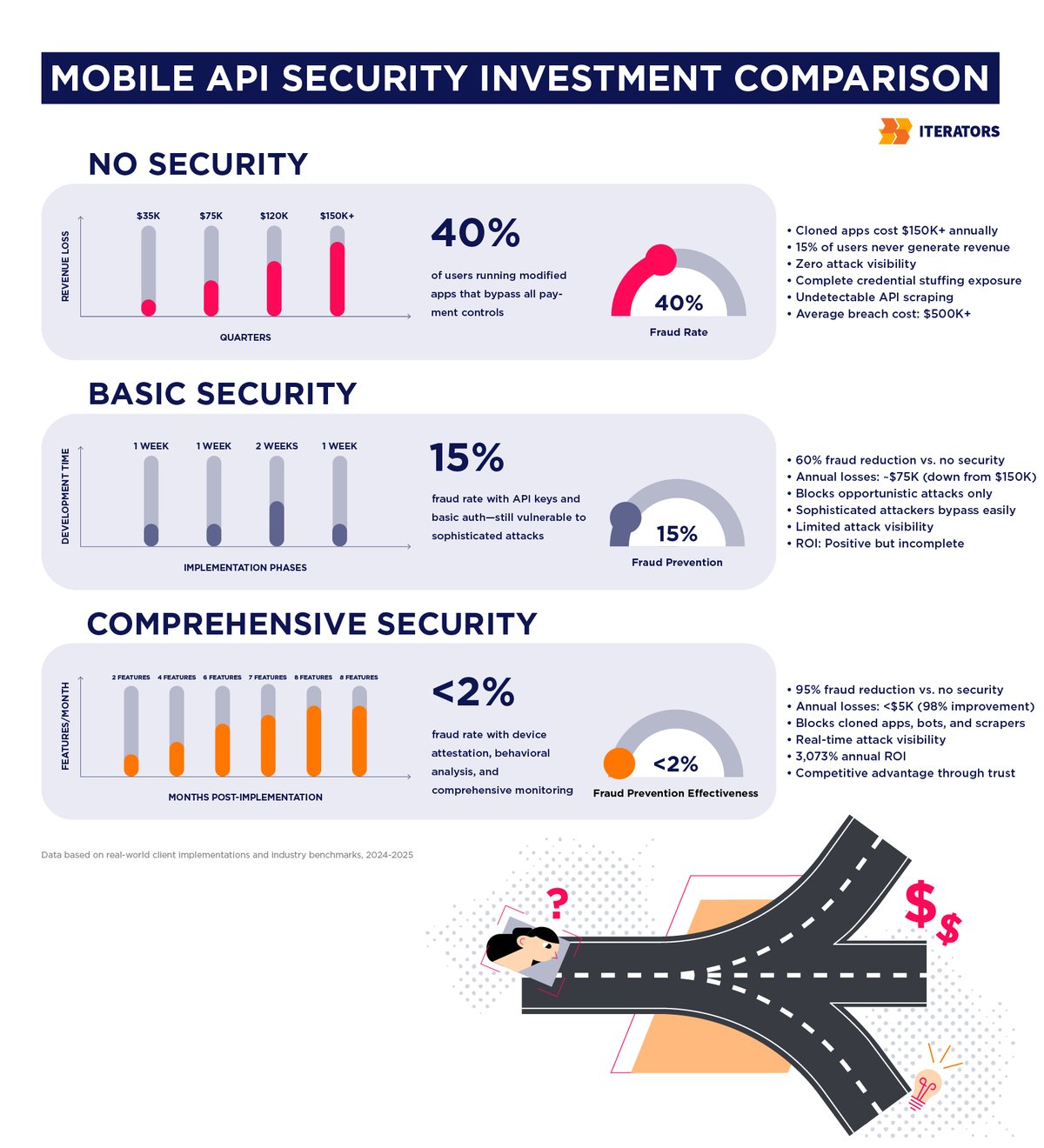
Revenue loss: If your app uses in-app purchases or subscriptions, cloned apps can bypass payment entirely. One fintech client we worked with discovered that 15% of their “active users” were actually running modified APKs that unlocked premium features without paying.
Data breaches: Mobile APIs often expose more data than necessary because developers optimize for offline functionality. If an attacker can scrape your API, they can build competing services using your data.
Reputation damage: When your API gets credential-stuffed and user accounts are compromised, users blame you—not the bot network that attacked you.
Compliance violations: GDPR, HIPAA, and PCI-DSS all have specific requirements for data protection. If your mobile API leaks personally identifiable information because you didn’t implement proper mobile API security measures like device attestation, you’re liable.
The mobile API security stakes are high. Let’s look at how attackers actually exploit mobile APIs.
Common Mobile API Security Threats and Exploitation Patterns
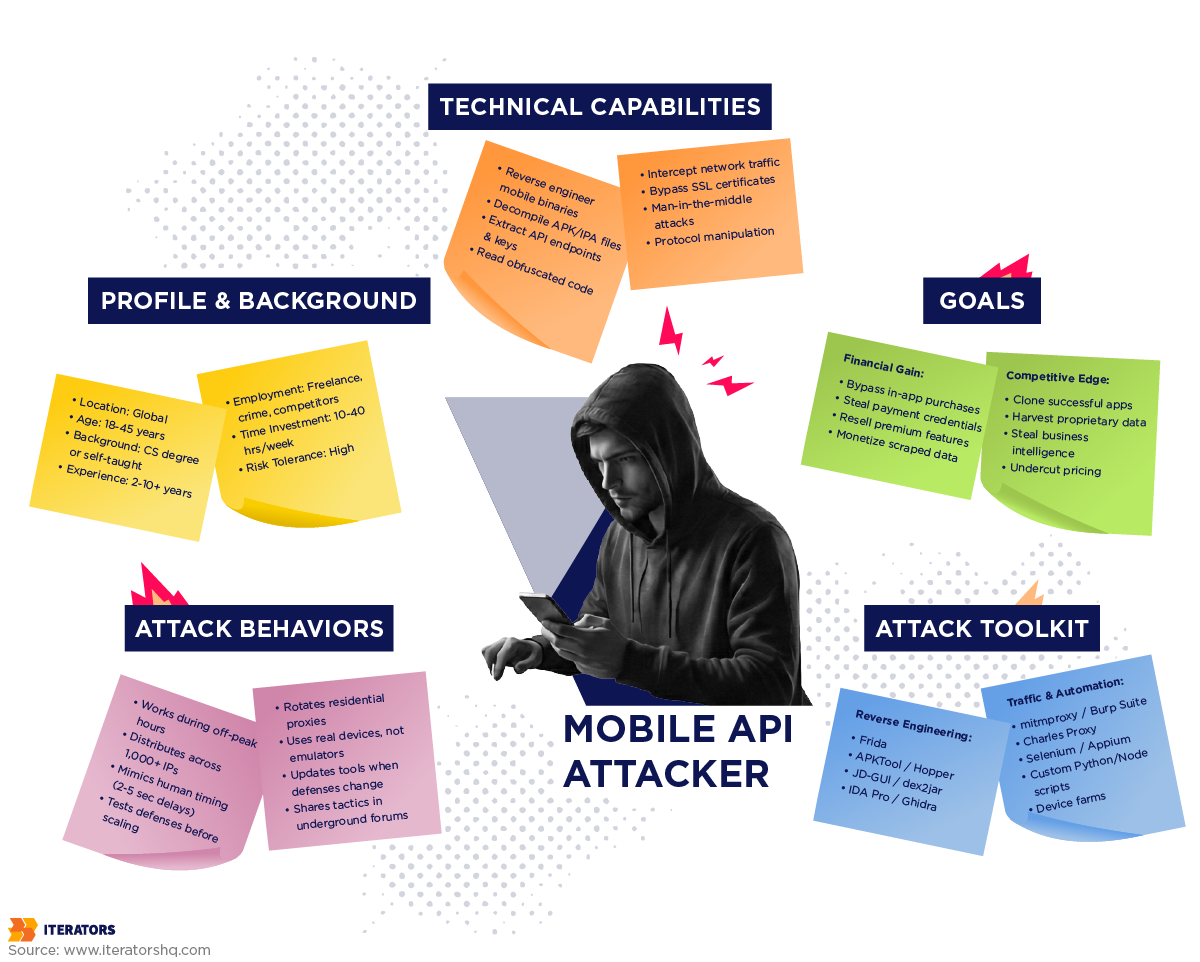
Understanding attack patterns is the first step to defending against them. Here are the most common—and most damaging—mobile API security threats in 2025.
Credential Stuffing Attacks
What it is: Attackers take username/password combinations leaked from other breaches and systematically test them against your login API.
Why mobile API security is harder: Mobile apps often implement “remember me” functionality that stores credentials locally. If users reuse passwords across services (and they do), attackers can automate login attempts at massive scale.
Real-world impact: We’ve seen credential stuffing attacks generate 100,000+ login attempts per hour against mobile APIs. Because mobile apps typically don’t implement CAPTCHA (it destroys UX), these attacks succeed at alarming rates.
What makes it hard to detect: Attackers distribute requests across thousands of IP addresses using residential proxies. Your rate limiting sees each IP making just 2-3 requests per hour—perfectly normal user behavior.
The tell-tale sign: Sudden spikes in failed login attempts followed by successful logins from new devices/locations. If you’re not monitoring authentication patterns, you won’t notice until users report unauthorized access.
API Scraping and Data Harvesting
What it is: Automated tools that systematically call your API endpoints to extract all available data.
Why mobile makes it worse: Mobile APIs are designed for efficient data transfer, often returning large JSON payloads. Attackers can reverse-engineer your app to find these endpoints and call them directly.
Real-world example: A competitor to one of our clients built their entire product database by scraping a mobile API that returned full product catalogs. The API had authentication, but the attacker simply created free accounts and automated the requests.
The business damage: Not just lost competitive advantage—the scraped data included pricing information, inventory levels, and supplier details. The client lost major contracts when competitors undercut them using this intelligence.
What makes it particularly damaging for mobile API security: Unlike web scraping, which leaves obvious server logs, API scraping looks like legitimate app usage. You can’t easily distinguish between a real user browsing 1,000 products and a bot scraping them.
Request Replay Attacks
What it is: Attackers intercept a legitimate API request and replay it multiple times to trigger unintended actions.
Why mobile makes it worse: Mobile apps often cache requests when offline, then replay them when connectivity returns. Attackers can exploit this pattern to duplicate transactions.
Classic scenario: A payment API that doesn’t implement idempotency keys. User taps “Pay” once. The network is slow. App retries the request. User gets charged twice. Now imagine an attacker deliberately replaying that request 100 times.
Another variation: Promo code abuse. An attacker intercepts the API call that applies a “first-time user” discount, extracts the request parameters, and replays it on multiple accounts.
The financial impact: One e-commerce client lost $47,000 in a single weekend because their “apply discount” endpoint could be replayed unlimited times. The attacker created a script that applied a 50% discount to thousands of orders.
Cloned and Modified Apps
What it is: Attackers decompile your app, modify the code to bypass restrictions, and redistribute the modified version.
Why this is the ultimate mobile threat: Unlike the other attacks, this one completely bypasses your client-side security. The attacker controls the entire client environment.
Common modifications:
- Remove in-app purchase checks (unlock premium features)
- Bypass subscription validation
- Remove ads
- Inject malware
- Redirect API calls to attacker-controlled servers
Distribution channels: Third-party app stores, torrent sites, “modded APK” websites. Some modified apps get millions of downloads.
Real-world case: A mobile game client we consulted for discovered that 40% of their Android users were running modified APKs that unlocked all in-app purchases. They were serving infrastructure costs for millions of users who would never pay.
The detection challenge: Modified apps often use the same API keys and authentication tokens as legitimate apps. From the backend perspective, they look identical.
Bot Network Targeting
What it is: Coordinated attacks using thousands of compromised devices or cloud instances to overwhelm your API or execute fraud at scale.
Why mobile APIs are vulnerable: Mobile backends are optimized for high concurrency to handle legitimate traffic spikes. This same architecture makes them attractive targets for bot networks.
Attack patterns:
- Inventory hoarding: Bots reserve limited inventory (concert tickets, sneaker drops) faster than humans can
- Referral fraud: Creating thousands of fake accounts to collect referral bonuses
- Content manipulation: Automated likes/follows/reviews to game ranking algorithms
- Resource exhaustion: Overwhelming your API to cause service degradation
The sophistication level: Modern bot networks use real mobile devices (device farms), rotate through residential IP addresses, and mimic human behavior patterns (random delays, realistic user agents).
Detection difficulty: A well-designed bot network is nearly indistinguishable from legitimate users. They pass basic security checks, maintain reasonable request rates, and exhibit “human-like” behavior.
These attack patterns represent just the beginning of mobile security challenges. For a broader perspective on how AI and machine learning are being used to combat cybersecurity threats, explore our analysis of generative AI in cybersecurity.
Building Mobile API Security: Backend Trust Signals and Defense Framework
Now that you understand the threats, let’s build mobile API security defenses. The key mobile API security insight: you cannot trust the mobile client. Your security architecture must verify every claim the client makes.
Mobile API Security Through Device Attestation and Integrity Checks
Device attestation is your first mobile API security line of defense. It answers the critical question: “Is this request coming from a legitimate, unmodified version of my app running on a real device?”
How it works:
- Your app requests an attestation token from the platform (Apple’s App Attest or Android’s Play Integrity API)
- The platform cryptographically signs a token proving the app binary hasn’t been modified
- Your backend verifies this signature before processing the request
What this prevents:
- Modified/cloned apps (the signature won’t match)
- Emulators and rooted devices (the platform refuses to attest)
- API requests from scripts/bots (no valid attestation token)
Implementation approach on iOS: Use the DeviceCheck framework to generate a key pair, create an attestation with a server-provided challenge, and send the attestation token to your backend for verification. Follow Apple’s App Attest documentation for detailed implementation guidance and security best practices.
Implementation approach on Android: Use the Play Integrity API with IntegrityManager to request integrity tokens with a nonce, then verify the token on your backend. Consult Google’s Play Integrity API guide for comprehensive implementation details and token verification processes.
Backend verification process: Decode the attestation token, parse the structure (CBOR for iOS), verify the signature chain, validate the challenge matches, and confirm the team/bundle ID or package name.
Critical implementation details:
- Never skip the nonce: Always include a server-generated challenge to prevent replay attacks
- Cache verification results: Attestation is expensive—cache the result for the session
- Graceful degradation: Don’t block all users if attestation fails (some legitimate devices can’t attest). Instead, flag them for additional scrutiny.
Limitations to understand:
Device attestation is not foolproof. Sophisticated attackers can:
- Use device farms with real, non-rooted devices
- Exploit zero-day vulnerabilities in the attestation APIs
- Social-engineer users into installing certificates that bypass checks
Think of attestation as a strong filter, not an impenetrable wall.
Request Validation Frameworks
Every mobile API security implementation should include multiple validation layers before reaching your business logic.
Layer 1: Schema Validation
Validate that the request structure matches your API contract. Use strong typing to ensure amounts are valid numbers, currencies match allowed values, user IDs exist, and payment methods are legitimate.
Key validation rules include:
- Amount must be positive and within reasonable bounds
- Currency must be from an approved list
- User identifiers must follow expected formats
- Payment method IDs must be properly formatted
Layer 2: Rate Limiting
Prevent abuse by limiting request frequency. Implement a sliding window approach that tracks requests per identifier (user ID, IP address, device ID) over a time period.
Rate limiting configuration should include:
- Maximum requests per time window
- Burst allowance for legitimate traffic spikes
- Different limits for different endpoint types
- Grace period before hard blocking
Layer 3: Behavioral Analysis
Detect anomalous patterns that suggest automated abuse by analyzing request fingerprints including user ID, endpoint, timestamp, user agent, IP address, and device ID.
Behavioral signals to monitor:
- Request timing: Human users have variable timing; bots have suspiciously consistent intervals
- Endpoint diversity: Real users navigate naturally; scrapers target specific endpoints repetitively
- Device consistency: Legitimate users typically use the same device; account takeovers show device switching
- Geographic anomalies: Sudden location changes that defy physics suggest credential sharing or theft
Advanced behavioral analysis increasingly leverages machine learning to detect subtle attack patterns. Learn about the differences between machine learning vs generative AI and how each approach can enhance mobile API security.
Mobile API Security: Authentication Best Practices
Mobile API security authentication has unique requirements that differ from web applications.
Use Short-Lived Access Tokens with Refresh Tokens
Implement a token pair system:
- Access tokens expire quickly (15 minutes) and grant API access
- Refresh tokens last longer (30 days) and can generate new access tokens
- Store refresh tokens in your database to enable revocation
- Verify refresh tokens haven’t been revoked before issuing new access tokens
This approach minimizes the damage if an access token is compromised while maintaining a smooth user experience.
This token-based approach follows the OAuth 2.0 Authorization Framework specification for secure API authorization.
Implement Biometric Step-Up Authentication
For sensitive operations (payments, account changes), require biometric confirmation using platform capabilities like Face ID, Touch ID, or Android Biometric APIs.
Implementation approach:
- Check if biometric authentication is available on the device
- For supported devices, use biometric policy for sensitive operations
- Fall back to device passcode if biometrics aren’t available
- Always perform this check on the device, then validate the action on the backend
Certificate Pinning Implementation
Certificate pinning prevents man-in-the-middle attacks by ensuring your app only trusts your specific SSL certificate.
iOS Implementation approach:
- Store your certificate in the app bundle as a .cer file
- Implement a custom URLSessionDelegate
- In the authentication challenge handler, compare the server’s certificate against your pinned certificates
- Only accept the connection if the certificates match
Android Implementation approach:
- Use OkHttp’s CertificatePinner
- Add SHA-256 hashes of your certificates to the pinner configuration
- The library automatically validates server certificates against your pins
Critical considerations:
Pin backup certificates: Always pin at least two certificates (current + backup) to avoid bricking your app during certificate rotation
Plan for certificate rotation: Build an update mechanism that can refresh pins without requiring an app update
Monitor pinning failures: Log (don’t just silently fail) when pinning fails—it might indicate an attack
Multi-Platform Security Challenges

Implementing mobile API security means supporting iOS and Android—platforms with fundamentally different security models and capabilities. Each platform requires specific mobile API security considerations.
Platform-Specific Security Features
iOS Security Strengths:
- Keychain: Hardware-backed secure storage for credentials
- App Attest: Strong device attestation
- Mandatory App Store Review: Reduces malware distribution
- Unified OS Updates: Most users run recent iOS versions
iOS Security Weaknesses:
- Jailbreaking: Still possible on many devices
- Limited background execution: Makes certain security checks harder
- Certificate pinning complexity: Requires careful implementation
Android Security Strengths:
- Play Integrity API: Robust device attestation
- Keystore: Hardware-backed key storage
- Larger security research community: Vulnerabilities get discovered faster
Android Security Weaknesses:
- Fragmentation: Thousands of device models, many running outdated OS versions
- Side-loading: Users can install apps from unknown sources
- Custom ROMs: Completely bypass platform security
- Rooting: More common and easier than iOS jailbreaking
Cross-Platform Framework Considerations
React Native and Flutter introduce additional mobile API security complexity.
React Native Mobile API Security Challenges:
The JavaScript bridge creates attack surfaces. Sensitive logic exposed in JavaScript can be easily extracted from the bundle, including API keys, payment processing logic, and business rules.
The correct approach: Move sensitive operations to native modules. API keys should never be exposed to JavaScript. Instead, create native modules (in Swift/Objective-C for iOS, Kotlin/Java for Android) that handle sensitive operations. The JavaScript layer only calls these native modules and receives results.
Example of the secure pattern:
- JavaScript requests a sensitive operation (like payment processing)
- Native module retrieves secrets from platform-secure storage (Keychain/Keystore)
- Native module executes the operation
- JavaScript receives only the result, never the sensitive data
Flutter Security Challenges:
Flutter apps are slightly harder to reverse-engineer than React Native (compiled to native code rather than JavaScript), but still vulnerable. Never store secrets directly in Dart code.
The secure approach: Use platform channels to access native secure storage. Create method channels that communicate with platform-specific code (Swift for iOS, Kotlin for Android) to retrieve secrets from Keychain or Keystore.
Maintaining Consistent Security Across Platforms
Strategy 1: Backend-Enforced Security
Never rely on client-side checks alone. Platform-specific receipt validation should happen on the backend:
- Validate Apple receipts through Apple’s verification service
- Validate Google Play receipts through Google’s verification API
- Verify the receipt matches the claimed purchase
- Check that product IDs and user IDs align
- Prevent replay of the same receipt
Strategy 2: Unified Security SDK
Build a shared security module that wraps platform-specific implementations using technologies like Kotlin Multiplatform. Define common interfaces for secure storage, device attestation, and other security primitives, then implement them natively for each platform.
The shared module provides a consistent API while leveraging platform-specific secure storage (Keychain for iOS, EncryptedSharedPreferences for Android) and attestation mechanisms.
Mobile API Security Architecture: Building Resilient Systems
Mobile API security isn’t just about individual features—it’s about how your entire system is structured to defend against threats.
The Mobile API Security Defense-in-Depth Model
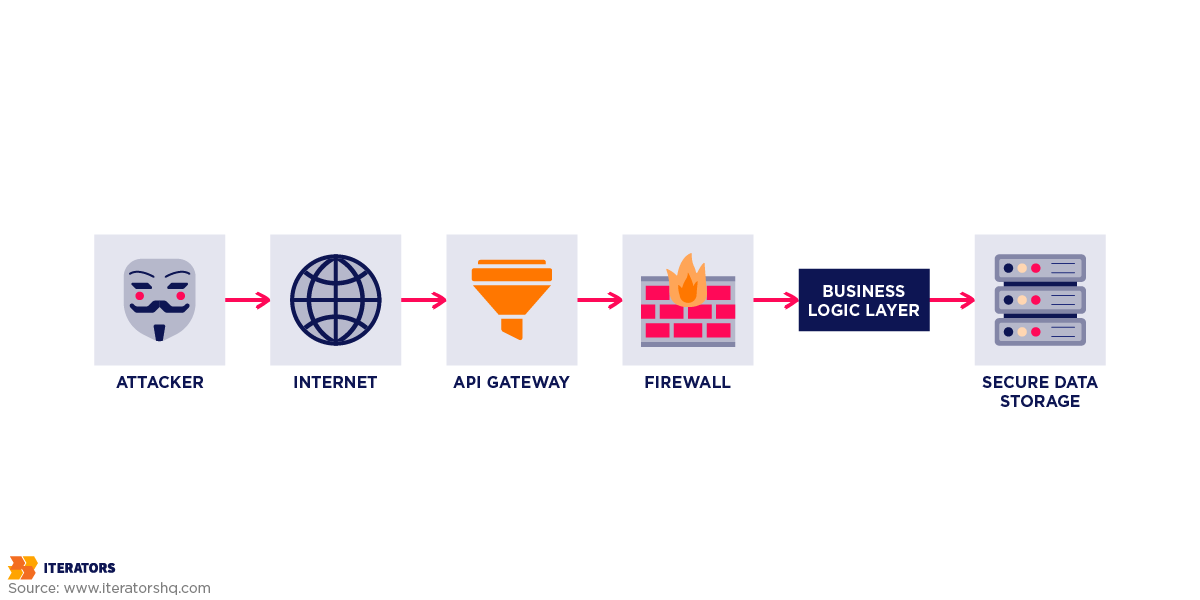
Effective mobile API security requires layered controls so that if one fails, others still protect you:
Layer 1: Network (CDN, DDoS Protection)
Layer 2: API Gateway (Rate Limiting, WAF)
Layer 3: Authentication (Device Attestation, OAuth)
Layer 4: Authorization (RBAC, Resource Permissions)
Layer 5: Business Logic (Input Validation, Fraud Checks)
Layer 6: Data Access (Encryption, Audit Logging)
Each layer should implement rate limiting, authentication, authorization, and validated business logic routing to create redundant protection.
This layered security approach aligns with the NIST Cybersecurity Framework principles for building resilient information systems.
API Gateway Configuration
Your API gateway is the first line of defense. Configure it properly with:
Rate limiting:
- Burst limits for short-term traffic spikes
- Sustained rate limits for normal operations
- Daily or monthly quotas to prevent long-term abuse
Web Application Firewall (WAF) rules:
- Rate-based blocking for excessive requests from single IPs
- Geographic restrictions for high-risk regions
- SQL injection and XSS protection
- Custom rules for your specific threat model
Monitoring and Observability
You can’t secure what you can’t see. Implement comprehensive mobile API security monitoring that tracks:
Security metrics:
- Authentication failures by user and IP
- Rate limit violations
- API latency and performance
- Device attestation failures
Recording suspicious activity:
- Log security events with full context
- Store events in immutable audit logs
- Alert the security team when thresholds are exceeded
- Track patterns across users and time periods
Key metrics to monitor:
- Failed authentication attempts per user/IP
- Rate limit violations
- Device attestation failures
- Unusual API usage patterns (e.g., same endpoint called 1000 times)
- Geographic anomalies (user in US, then Russia 5 minutes later)
- Token refresh frequency
- API error rates
Set up alerts for:
- Sudden spike in authentication failures (possible credential stuffing)
- High rate of attestation failures (cloned app distribution?)
- Unusual geographic patterns (account takeover?)
- API latency spikes (DDoS attack?)
Balancing Mobile API Security and User Experience

The harsh reality of mobile API security: every security measure adds friction. Your job is to add the minimum friction necessary to achieve your security goals.
Performance Impact Mitigation
Problem: Device attestation adds 200-500ms latency to every request.
Solution: Cache attestation results. Store validated attestations with device ID, validation timestamp, and validity status. Check the cache first:
- If no cached result exists, perform full attestation
- If cached result is recent (e.g., within 1 hour), use it
- If cached result is expired, re-verify
This reduces the performance impact to only the first request in each session.
Graceful Degradation Strategies
Don’t block users when security checks fail—flag them for additional scrutiny instead.
Define security levels:
- Trusted: All checks passed, known device, good behavior history
- Suspicious: Some checks failed but other signals are positive
- Blocked: Multiple red flags indicate high risk
Security level determination:
- Perfect case: attestation passed, known device, low behavior score = Trusted
- Attestation failed but known device with good history = Suspicious (allow but monitor)
- New device but passed attestation = Suspicious
- Multiple red flags = Blocked
Applying security levels:
- Trusted users get normal access
- Suspicious users may require step-up authentication for sensitive operations
- Blocked users receive clear error messages
User Communication Best Practices
When you do need to block a user, communicate clearly:
Bad example: “Error: Request failed (403)”
Good example: “For your security, we need to verify your identity. Please confirm your email or use biometric authentication.”
Bad example: “Rate limit exceeded”
Good example: “You’re moving too fast! Please wait 60 seconds before trying again. This helps us keep your account secure.”
A/B Testing Security Measures
Not sure if a security measure will hurt conversion? Test it.
Split users into groups and measure the impact:
- Assign users consistently to test variants based on user ID hash
- One group gets strict security enforcement
- Another group gets lenient enforcement
- Track conversion metrics for both groups
- Analyze whether security measures impact user behavior
This data-driven approach lets you make informed decisions about security trade-offs.
Measuring Mobile API Security ROI
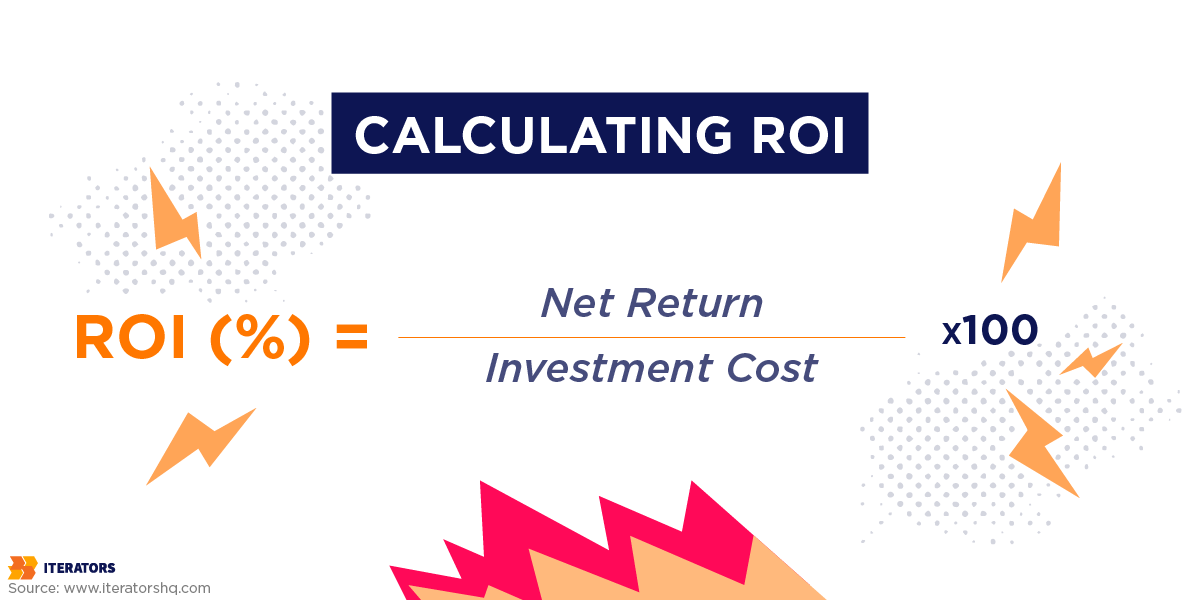
Mobile API security is an investment. Here’s how to prove it’s worth it.
Metrics That Matter
Attack Prevention Metrics:
- Blocked credential stuffing attempts
- Prevented API scraping (estimated)
- Cloned app downloads prevented
- Fraudulent transactions blocked
Business Impact Metrics:
- Revenue protected (blocked fraud amount)
- Data breach costs avoided
- Customer trust score (NPS correlation with security features)
- Compliance fines avoided
Operational Metrics:
- Security incident response time
- Time to patch vulnerabilities
- False positive rate (legitimate users blocked)
Cost-Benefit Analysis Example
Let’s say you’re considering implementing device attestation:
Costs:
- Development: 2 weeks × $10,000/week = $20,000
- Ongoing infrastructure: $500/month
- Performance impact: 5% increase in API latency
Benefits (annual):
- Prevented cloned app revenue loss: $150,000
- Reduced fraud: $75,000
- Avoided data breach: $500,000 (estimated)
- Improved user trust → 2% conversion increase: $100,000
ROI: ($825,000 – $26,000) / $26,000 = 3,073% annual ROI
Even if you’re conservative and only count direct fraud prevention: ($75,000 – $26,000) / $26,000 = 188% annual ROI
These ROI calculations are based on real-world implementations. To see detailed examples of how we’ve helped clients implement secure, scalable mobile API solutions, explore our case studies showcasing measurable security and business outcomes.
Conclusion: Mobile API Security as a Competitive Advantage
Here’s what we’ve covered about mobile API security:
The fundamental problem: Traditional API security fails for mobile because mobile API security requires trusting neither the client nor the environment.
The attack landscape: Credential stuffing, API scraping, replay attacks, cloned apps, and bot networks are actively targeting mobile APIs right now.
The defense framework: Device attestation, request validation, proper authentication, certificate pinning, and behavioral analysis work together to build resilient systems.
The platform challenge: iOS and Android have different security models. Cross-platform frameworks add complexity. You need consistent security regardless of how users access your API.
The architecture imperative: Defense-in-depth, proper monitoring, and graceful degradation ensure your security actually works in production.
The UX balance: Security doesn’t have to destroy user experience. Cache attestation results, use step-up authentication only when necessary, and communicate clearly when security measures activate.
The companies that will win in mobile aren’t just building great apps—they’re building trustworthy systems with robust mobile API security that users can rely on. Security isn’t a cost center; it’s a competitive advantage.
When your competitor’s API gets scraped and their business model collapses, you’ll still be standing. When the next major credential stuffing attack hits your industry, your users won’t be affected. When regulators start enforcing stricter data protection requirements, you’ll already be compliant.
Start with these three actions:
- Implement device attestation this week. It’s the single highest-impact security measure you can add.
- Audit your authentication flow. Are you using short-lived tokens? Is biometric step-up enabled for sensitive operations? Are tokens stored securely?
- Set up security monitoring. You can’t defend against attacks you can’t see. Track authentication failures, rate limit violations, and unusual patterns.
Mobile API security isn’t optional anymore. The question is whether you’ll build resilient systems proactively or reactively—after an attack forces your hand.
FAQ
Q: How much does device attestation slow down API requests?
Device attestation typically adds 200-500ms of latency to the initial request. However, you can cache attestation results for 1-24 hours depending on your security requirements, so subsequent requests have zero additional latency. For most applications, this is an acceptable trade-off for the security benefits.
Q: Can device attestation be bypassed?
Sophisticated attackers with access to real, non-rooted devices can bypass attestation. However, this significantly raises the cost of attack. Most opportunistic attackers (scrapers, bot networks) will move to easier targets. Think of attestation as a strong filter, not an impenetrable wall.
Q: Should I implement certificate pinning for my mobile app?
It depends on your threat model. If you’re handling financial transactions, health data, or other sensitive information, yes—absolutely implement certificate pinning. For less sensitive applications, the operational complexity (handling certificate rotation) might outweigh the benefits. At minimum, ensure you’re using TLS 1.3 with strong cipher suites.
Q: How do I handle security for older app versions still in production?
Implement API versioning with different security requirements per version. Newer API versions can enforce stricter security (device attestation, shorter token lifetimes) while older versions use more lenient checks. Set a sunset date for old API versions and force users to update eventually.
Q: What’s the best way to detect API scraping?
Look for patterns: high request volume from single users, low endpoint diversity (targeting specific data endpoints), suspiciously consistent request timing, and rapid sequential access to paginated resources. Implement behavioral analysis that flags users exhibiting these patterns for additional scrutiny.
Q: How do I balance security with app performance?
Cache security checks (attestation results, rate limit counters), use asynchronous validation where possible, implement security checks at the API gateway layer (reducing backend load), and use step-up authentication only for sensitive operations rather than every request.
Q: Should I build security in-house or use third-party services?
For core authentication and authorization, build in-house using proven libraries (OAuth, JWT). For specialized security (fraud detection, bot mitigation), consider third-party services—they have more data and expertise. For device attestation, use platform-provided APIs (App Attest, Play Integrity) rather than rolling your own.
Q: What is mobile API security and why is it different from web API security?
Mobile API security is the practice of protecting APIs that serve mobile applications from threats like credential stuffing, API scraping, cloned apps, and bot networks. It differs from web API security because mobile apps run on uncontrolled devices where attackers can reverse-engineer code, intercept traffic, and modify app behavior—creating unique attack surfaces that don’t exist in web environments.
Need help implementing mobile API security for your application? Our custom software development services have helped fintech, healthcare, and e-commerce clients build secure mobile API solutions handling millions of daily requests. Schedule a consultation to discuss your specific mobile API security requirements.