You’ve built something incredible. Your product solves real problems, your early customers love it, and your sales team just landed a meeting with a Fortune 500 company. The deal could be worth more than all your current contracts combined. But there’s one final hurdle standing between you and that signature: the Enterprise Vendor Assessment – a comprehensive security evaluation that can either accelerate your deal or kill it completely.
Then the email arrives: “Before we proceed, please complete our Enterprise Vendor Assessment.”
Attached is a 300-question spreadsheet that looks like it was designed by a committee of lawyers, security architects, and people who genuinely enjoy making others suffer. Questions like “Describe your cryptographic key rotation procedures” and “Provide evidence of your last disaster recovery test” make you realize that your “move fast and break things” startup culture is about to collide with enterprise reality.
Welcome to the Enterprise Vendor Assessment—the gauntlet every B2B SaaS company must run to unlock those sweet, sweet enterprise contracts.
Here’s the brutal truth: 61% of U.S. companies have experienced a data breach caused by a third-party vendor. When your prospective customer asks invasive questions about your architecture during their Enterprise Vendor Assessment process, they’re not being difficult. They’re protecting themselves from becoming another statistic in next year’s breach report.
But here’s the good news: if you architect your product correctly from the start, these assessments transform from deal-killers into deal-accelerators. While your competitors spend weeks scrambling to answer basic security questions, you’ll send over your pre-built security documentation and move straight to contract negotiation.
This guide will show you exactly how to build an assessment-ready architecture that enterprise customers trust—without sacrificing the agility that makes startups dangerous.
Want expert help building your enterprise-ready architecture? Work with us at Iterators to schedule a free consultation and get personalized guidance on passing vendor assessments and closing enterprise deals faster.
Why Enterprise Vendor Assessments Actually Matter (Beyond Checking Boxes)

Let’s talk about what’s really happening during an Enterprise Vendor Assessment.
Enterprise sales cycles are already painfully long—averaging seven months or more compared to the 1-3 month cycles typical for SMB deals. A significant chunk of that delay comes from security reviews and compliance verification. When enterprises ask for SOC 2 reports, penetration test results, and architectural diagrams, they’re not just being bureaucratic. They’re performing due diligence because the average data breach costs over $4 million, and regulations like GDPR and CCPA impose massive penalties for mishandling data.
Think of the Enterprise Vendor Assessment as a “trust gap” that you need to bridge. The enterprise is essentially asking: “If we give you access to our customer data, employee information, or business-critical systems, will you protect it as well as we would?”
Your architecture is your answer to that question.
The Real Cost of Being Unprepared for Enterprise Vendor Assessments
When you can’t quickly demonstrate security maturity during an Enterprise Vendor Assessment, several painful things happen:
Time kills deals. Security questionnaires can delay deals for weeks or even months. In competitive markets, the company that can prove security fastest often wins, regardless of feature superiority.
You lose negotiating leverage. When security concerns dominate the conversation, you’re suddenly defending your product instead of selling its value. Price discussions shift from “what’s this worth?” to “what discount will you give us to offset the risk?”
You waste engineering resources. Without proper documentation and architecture, your CTO spends days answering the same Enterprise Vendor Assessment questions repeatedly instead of building product. Every new enterprise deal triggers another fire drill.
You can’t scale upmarket. If every enterprise deal requires custom security work, you’ve built a consulting business, not a scalable SaaS company.
The companies that win enterprise deals consistently treat security architecture as a product feature, not an afterthought—making Enterprise Vendor Assessment responses part of their competitive advantage.
The Five Pillars of Assessment-Ready Architecture for Enterprise Vendor Assessment Success
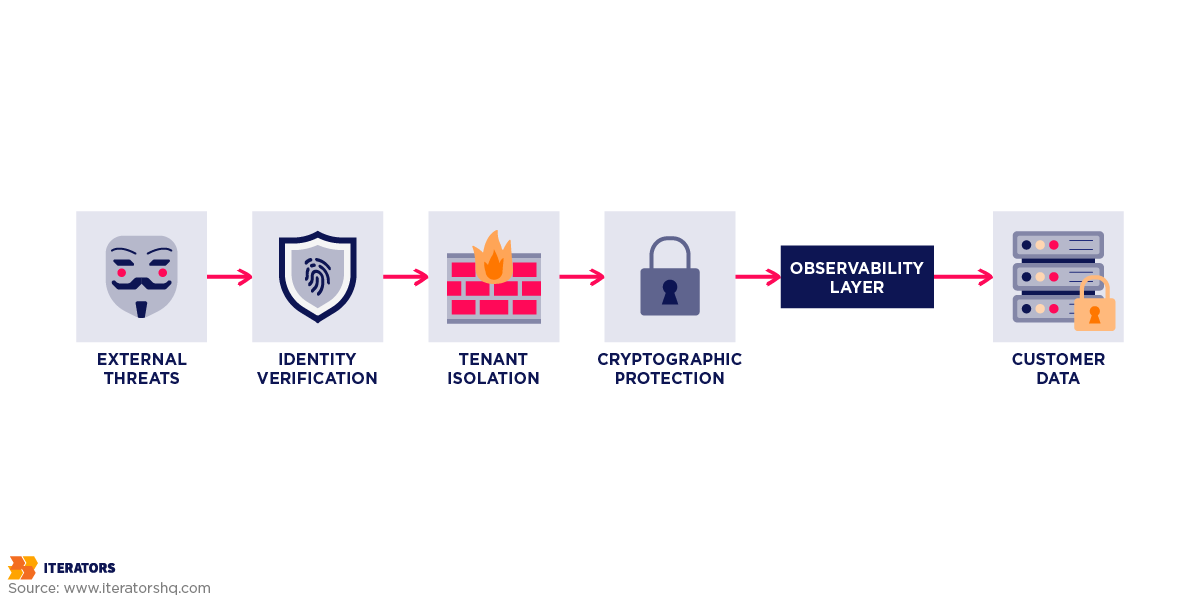
Before we dive into specific technical requirements, let’s establish the foundational principles that make your architecture defensible during Enterprise Vendor Assessments.
1. Identity and Access Management: Your Digital Front Door
If you take nothing else from this guide, remember this: enterprise customers will not adopt your product if it requires manual user management or username/password authentication.
Why? Because every username/password combination is a security vulnerability waiting to happen. Users reuse passwords, forget to rotate them, and—most critically—cannot be instantly de-provisioned when they leave the company.
Single Sign-On (SSO) Is Non-Negotiable
When an enterprise employee logs into your application, they should do so through their corporate identity provider (like Okta, Azure AD, or Google Workspace), not by creating yet another username and password.
The two protocols you need to support for successful Enterprise Vendor Assessment outcomes are:
SAML 2.0 remains the enterprise standard, despite being XML-based and somewhat archaic. Your architecture needs endpoints that can receive and validate SAML assertions, verify digital signatures, and map enterprise attributes (email, name, department) to your internal user model.
OpenID Connect (OIDC) is the more modern, JSON-friendly alternative built on OAuth 2.0. While SAML dominates in legacy enterprises, OIDC is gaining ground, especially with cloud-native companies.
A truly enterprise-ready product supports both.
But here’s where most startups stop—and where you should go further.
Just-in-Time (JIT) Provisioning
Instead of requiring an admin to manually create user accounts, implement JIT provisioning. When an employee clicks your app icon in their corporate dashboard, your system receives the SAML assertion, sees the user doesn’t exist yet, and automatically creates their account based on the attributes provided.
This reduces administrative friction to nearly zero—a massive selling point when your champion is trying to get budget approval and answers Enterprise Vendor Assessment questions.
Directory Synchronization (SCIM)
SSO handles authentication (letting people in), but what about de-provisioning (kicking people out)?
When an employee is terminated, their access to your platform must be revoked immediately. If you only rely on SSO, they might still have an active session token for hours or days.
The solution is SCIM (System for Cross-domain Identity Management). By implementing a SCIM API, you allow the enterprise’s identity provider to “push” updates to your system. When someone is disabled in Active Directory, your platform receives a SCIM signal to lock the account and revoke all tokens.
Supporting SCIM is a strong signal of enterprise maturity and directly addresses one of the top audit findings in Enterprise Vendor Assessments: “zombie accounts” (former employees who still have access).
Role-Based Access Control (RBAC)
An enterprise buyer will have users with wildly different needs—financial auditors who need read-only access to billing data, content editors who can modify certain records, system administrators with full control, and compliance officers who need to see audit logs.
A simple “Admin vs. User” permission model won’t cut it in Enterprise Vendor Assessment scenarios.
Your authorization logic needs to be:
- Granular: Users should have access to only what they need (principle of least privilege)
- Flexible: Enterprises should be able to define custom roles that match their internal job descriptions
- Decoupled: Don’t hardcode permission checks throughout your business logic. Use a permission-based system where roles are collections of permissions (like can_edit_invoices, can_view_audit_logs)
When an auditor asks “Can you demonstrate that users only have access to data required for their job function?” during an Enterprise Vendor Assessment, you want to confidently show them your RBAC configuration, not scramble to grep your codebase for scattered permission checks.
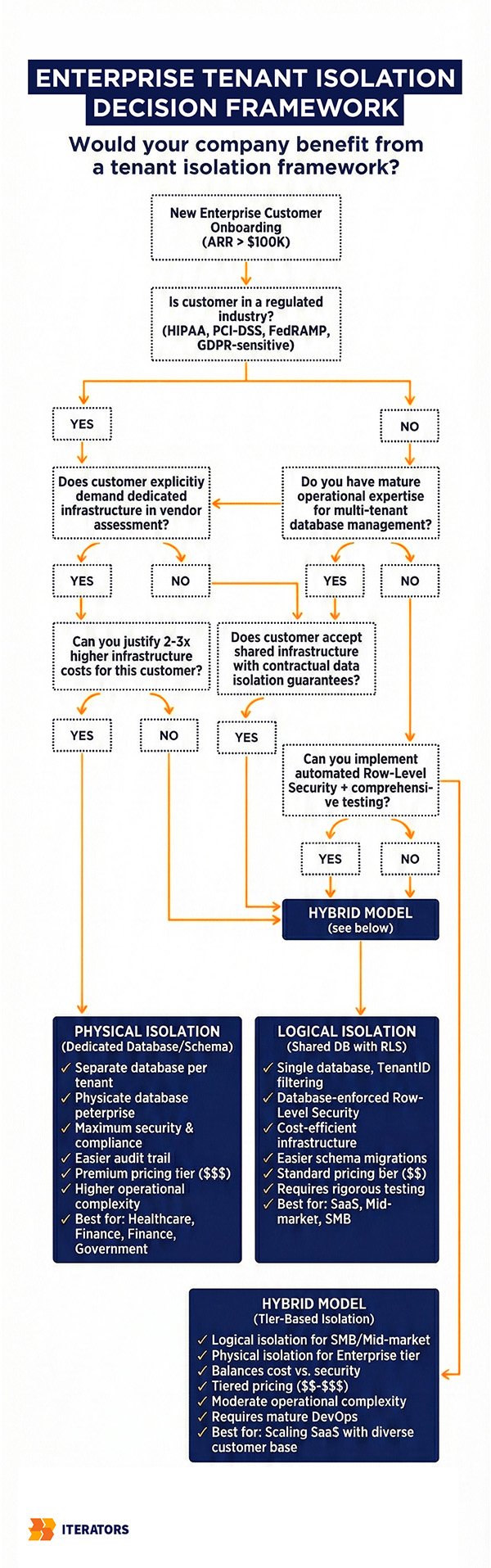
2. Tenant Isolation: Proving Data Cannot Leak
The nightmare scenario for any enterprise customer conducting an Enterprise Vendor Assessment is simple: their proprietary data leaking to a competitor who happens to use the same SaaS platform.
During Enterprise Vendor Assessments, you’ll face pointed questions about how you isolate customer data. Your answer determines whether you pass or fail the “Confidentiality” criteria in SOC 2 audits.
The Isolation Spectrum
There are two primary approaches to multi-tenant architecture, each with distinct trade-offs that affect Enterprise Vendor Assessment outcomes:
Logical Isolation (The “Pool” Model)
All customers share the same database tables, with data segregated by a TenantID column.
Advantages: Simple to deploy, cost-efficient, easy to manage schema migrations.
Disadvantages: Auditors view this as the least secure model because a single missing WHERE tenant_id = ? clause in a SQL query can expose all data to the wrong customer.
If you use this model, you must demonstrate defense-in-depth during Enterprise Vendor Assessments:
- Row-Level Security (RLS): Use database-native features (like PostgreSQL’s RLS policies) to enforce isolation at the database engine level. Set a session variable when a user authenticates, and the database automatically filters all queries to only return rows for that tenant.
- Automated Testing: Provide evidence of integration tests that specifically attempt cross-tenant data access and prove they fail.
- Query Auditing: Show that your database logs can be analyzed to detect potential cross-tenant queries.
Physical Isolation (The “Silo” Model)
Each customer gets dedicated resources—either a separate database schema, separate database instance, or completely isolated infrastructure.
Advantages: Maximum security. Physical/logical barriers prevent data leakage. Easier to pass Enterprise Vendor Assessments for highly regulated industries (healthcare, finance).
Disadvantages: Operational complexity. Managing schema migrations across 1,000 separate databases is challenging. Higher infrastructure costs.
Many successful SaaS companies use a hybrid approach: logical isolation for SMB/mid-market customers, and silo isolation (at a premium price) for enterprise customers who demand it during their Enterprise Vendor Assessment process.
The “Noisy Neighbor” Problem
Beyond data leakage, enterprises conducting vendor assessments worry about performance isolation. If a small startup shares your infrastructure, a traffic spike from one tenant shouldn’t degrade service for others.
Your architecture should include:
- Rate limiting at the API gateway level, keyed by tenant ID
- Resource quotas that prevent any single tenant from monopolizing compute or storage
- Circuit breakers that can automatically “quarantine” a tenant abusing the system
During Enterprise Vendor Assessments, providing load testing reports that demonstrate graceful degradation under stress—without affecting other tenants—builds tremendous confidence.
Data Residency and Sovereignty
With GDPR in Europe and various state-level privacy laws in the U.S., the physical location of data has become an architectural constraint in Enterprise Vendor Assessments.
Enterprise customers, particularly in the EU, may demand that their data never leaves a specific geographic region. Your architecture must support “sharding by geography”—where a tenant is pinned to a specific deployment in a specific region.
This complicates your deployment pipeline, but it opens markets that are completely closed to U.S.-only infrastructure.
3. Cryptography: Beyond the Checkbox in Enterprise Vendor Assessments
When an auditor conducting an Enterprise Vendor Assessment asks “Is data encrypted?” they’re not looking for a simple yes/no answer. They want to understand your entire cryptographic strategy.
Encryption at Rest: Moving Beyond Defaults
Most cloud providers offer default encryption for storage (EBS volumes, S3 buckets). Enabling this is mandatory, but it’s considered the bare minimum for Enterprise Vendor Assessment purposes.
Enterprise auditors often ask: “Who controls the encryption keys?”
If your cloud provider manages the keys transparently, the enterprise considers the data theoretically vulnerable to the provider or government subpoenas.
Advanced implementations that strengthen Enterprise Vendor Assessment responses include:
Customer-Managed Keys (CMK): Use a Key Management Service where you control the key lifecycle, separate from the storage service.
Bring Your Own Key (BYOK): A premium feature where the customer generates encryption keys in their own Hardware Security Module (HSM) and grants your platform permission to use them. This gives the customer a “kill switch”—if they revoke the key, their data becomes instantly cryptographically inaccessible.
This feature alone can win deals with highly paranoid customers in defense and finance conducting rigorous Enterprise Vendor Assessments.
Field-Level Encryption
For highly sensitive fields (Social Security Numbers, API tokens, credit card numbers), volume encryption isn’t enough for Enterprise Vendor Assessment standards. A database administrator or attacker with database access can still read plaintext data.
The solution is application-level encryption—encrypting data within your application logic before it’s sent to the database, following OWASP Enterprise Security Architecture best practices. This ensures that even a full database dump yields only ciphertext.
The trade-off? Searchability. You can’t easily query WHERE ssn = ‘…’ if the SSN is encrypted. You’ll need to use deterministic encryption schemes or accept that certain fields cannot be searched.
Encryption in Transit: The Entire Path
TLS 1.2+ is the baseline for any internet-facing service. But enterprises conducting vendor assessments assess the entire communication path.
If TLS terminates at your load balancer, is the traffic from the load balancer to your application servers unencrypted? In a zero-trust architecture aligned with the NIST Cybersecurity Framework, the answer must be “no.”
Modern implementations that satisfy Enterprise Vendor Assessment requirements include:
- Mutual TLS (mTLS) between microservices
- Service mesh architectures (like Istio) that enforce encryption for all inter-service communication
- Cipher suite hardening to disable weak algorithms
During Enterprise Vendor Assessments, auditors may scan your public endpoints using tools like SSL Labs. Having an “A+” rating with all weak ciphers disabled is table stakes.
Key Management Lifecycle
Encryption is only as strong as your key management, a critical focus area in Enterprise Vendor Assessments:
- Rotation: Keys should rotate automatically (at least annually)
- Separation of Duties: Developers who write code should not have access to production encryption keys
- Audit Trails: Every use of a cryptographic key should be logged (using CloudTrail or equivalent)
4. Operational Resilience: When Things Go Wrong
Your Service Level Agreement (SLA) is where engineering meets legal liability in Enterprise Vendor Assessment contexts. Enterprises demand high availability, but they also demand proof that you can recover from catastrophic failure.
Defining Your Recovery Objectives
Two metrics dominate disaster recovery conversations during Enterprise Vendor Assessments:
Recovery Time Objective (RTO): How long can you be down? (e.g., “We’ll restore service within 4 hours”)
Recovery Point Objective (RPO): How much data can you lose? (e.g., “We’ll lose no more than 1 hour of data”)
Here’s the trap: startups often agree to aggressive SLAs during Enterprise Vendor Assessment negotiations without the architecture to support them.
If your database backup runs every 24 hours, your RPO is 24 hours. Claiming 1 hour is a contractual liability you cannot fulfill.
To achieve low RPO that satisfies Enterprise Vendor Assessment requirements:
- Implement Point-in-Time Recovery (PITR) using transaction logs (like PostgreSQL’s WAL archives)
- Use continuous replication to a standby region, following patterns from the AWS Well-Architected Framework Security Pillar
- Enable automated snapshots at frequent intervals
Business Continuity Planning
Having backups isn’t enough for Enterprise Vendor Assessment purposes. You must prove they work.
Enterprises require evidence of annual disaster recovery tests. This means simulating a region failure or data corruption event and documenting the restoration process.
For early-stage startups, a documented “tabletop exercise” (simulating the decision-making process during an outage) can sometimes substitute for a full technical failover test—provided the technical capability exists—especially when responding to your first few Enterprise Vendor Assessments.
High Availability Architecture
Single points of failure (SPOFs) are red flags in Enterprise Vendor Assessments. Your architecture must demonstrate redundancy across at least multiple Availability Zones.
The difference between “three nines” (99.9% uptime = 8.7 hours downtime/year) and “four nines” (99.99% = 52 minutes/year) is enormous—both in cost and complexity.
Unless your contract value justifies it, resist committing to 99.99% during Enterprise Vendor Assessment negotiations. A “four nines” architecture requires multi-region active-active or active-passive setups, automated failover, and significant operational investment.
5. Observability: The Black Box Recorder
In the event of a security incident discovered during or after an Enterprise Vendor Assessment, the first question is always: “What happened?”
If your logs cannot answer this question, you’ve failed your duty of care.
Customer-Facing Audit Logs
Enterprise customers conducting vendor assessments often require an “Audit Log” feature within your application—allowing their admins to see what their users are doing.
Essential elements for Enterprise Vendor Assessment compliance:
- Who: User ID, IP address, user agent
- What: Action performed (Create, Read, Update, Delete), resource affected
- When: Timestamp (in UTC)
- Outcome: Success or failure
These logs should be immutable—stored in a way that prevents tampering, a critical requirement in Enterprise Vendor Assessments.
Internal System Logging
For your own security operations and to support Enterprise Vendor Assessment inquiries, comprehensive logging is mandatory:
- Authentication events: Successful and failed logins (critical for detecting brute-force attacks)
- Authorization events: Access to sensitive resources
- Privileged actions: Any command run by system administrators
- Data access: Queries against sensitive tables
Using structured formats (like JSON) makes these logs easier to ingest into analysis tools, simplifying Enterprise Vendor Assessment evidence collection.
SIEM Integration
A mature enterprise feature that accelerates Enterprise Vendor Assessment approval is the ability to stream audit logs to the customer’s Security Information and Event Management (SIEM) system (like Splunk or Datadog).
Provide a mechanism to push logs to an S3 bucket the customer owns, or an API endpoint they can poll. This allows enterprises to monitor activity within your platform in real-time, effectively extending their security perimeter to include your service—a major differentiator in competitive Enterprise Vendor Assessment scenarios.
Retention Policies
Compliance frameworks dictate retention periods (typically one year for security logs) that will be verified during Enterprise Vendor Assessments.
Your logging architecture should support lifecycle policies that automatically archive logs to cheaper storage (like AWS S3 Glacier) after a set period and delete them when retention expires. This ensures compliance without manual intervention.
The Software Supply Chain: Your Dependencies Are Your Liability in Enterprise Vendor Assessments

The SolarWindows and Log4j incidents fundamentally changed Enterprise Vendor Assessment processes. Enterprises now assume that your code isn’t the only risk—your dependencies are equally dangerous.
The Software Bill of Materials (SBOM)
Driven by Executive Order 14028 and similar regulations globally, the Software Bill of Materials is rapidly becoming a standard requirement in Enterprise Vendor Assessments.
An SBOM is a formal, machine-readable inventory of all components in your software—every open-source library, every framework, every dependency.
Minimum required elements for Enterprise Vendor Assessment purposes:
- Component name: (e.g., log4j-core)
- Version: (e.g., 2.14.1)
- Supplier: Who maintains it?
- Unique identifiers: CPE or PURL
- Dependency relationships: Is it direct or transitive?
Automating SBOM Generation
To make this operational for ongoing Enterprise Vendor Assessments, SBOM generation must be part of your CI/CD pipeline:
- Code commit triggers the build
- Build artifact (Docker image, JAR file) is created
- SBOM tool (like Syft or Trivy) scans the artifact and generates sbom.json
- Vulnerability scanner checks the SBOM against CVE databases
- Quality gate: If a critical CVE is found, the build fails
- Publish: If clean, the artifact and SBOM are published
The Trust Dividend
When a new zero-day vulnerability hits the news (like “Is your product vulnerable to CVE-2024-XXXXX?”), the prepared vendor conducting Enterprise Vendor Assessments can query their SBOM repository and answer with certainty in minutes.
The unprepared vendor spends days manually checking codebases, delaying their Enterprise Vendor Assessment response and eroding customer trust.
Compliance Frameworks as Engineering Blueprints for Enterprise Vendor Assessment Success

Many startups view compliance frameworks like SOC 2 or ISO 27001 as “paperwork.” This is a mistake that will haunt them during Enterprise Vendor Assessments.
Treat them as rigorous engineering specifications that provide a clear roadmap for architectural decisions that will be scrutinized in every Enterprise Vendor Assessment.
SOC 2 Type II: The De Facto Standard
For U.S.-based B2B SaaS companies, SOC 2 Type II is effectively non-negotiable for Enterprise Vendor Assessment purposes. It’s the primary mechanism for communicating trust to enterprise buyers.
The Trust Service Criteria (TSCs) evaluated in Enterprise Vendor Assessments:
- Security (Common Criteria): Required for everyone. Covers access control, monitoring, incident response
- Availability: Relevant if you offer strict SLAs
- Confidentiality: Relevant if you handle sensitive data (NDAs, trade secrets)
- Processing Integrity: Relevant for fintech/transactional systems
- Privacy: Relevant if you store PII (distinct from Confidentiality)
Type I vs. Type II:
A Type I report proves you designed the controls. A Type II report covers an observation period (usually 3-12 months) and tests operating effectiveness—the gold standard for Enterprise Vendor Assessments.
You cannot “cram” for a Type II. You must live the controls every day.
Continuous Compliance:
Platforms like Vanta, Drata, and Secureframe have revolutionized compliance by integrating with your cloud infrastructure to continuously monitor configuration. They alert you immediately if an S3 bucket becomes public or MFA is disabled.
This shifts compliance from an annual scramble to a daily operational metric, keeping you Enterprise Vendor Assessment-ready at all times.
ISO 27001: The International Standard
While SOC 2 dominates in North America, ISO 27001 is the international standard. It’s more prescriptive regarding the Information Security Management System (ISMS) and policy governance.
For startups expanding to Europe or Asia, ISO 27001 often becomes the primary requirement in international Enterprise Vendor Assessments.
NIST Cybersecurity Framework
The NIST CSF is gaining traction in Enterprise Vendor Assessments, particularly with government and critical infrastructure clients. It organizes activities into five functions: Identify, Protect, Detect, Respond, Recover.
Using this vocabulary in security questionnaires during Enterprise Vendor Assessments demonstrates alignment with federal standards and enterprise best practices.
Documentation as a Product: The Trust Center for Streamlined Enterprise Vendor Assessments
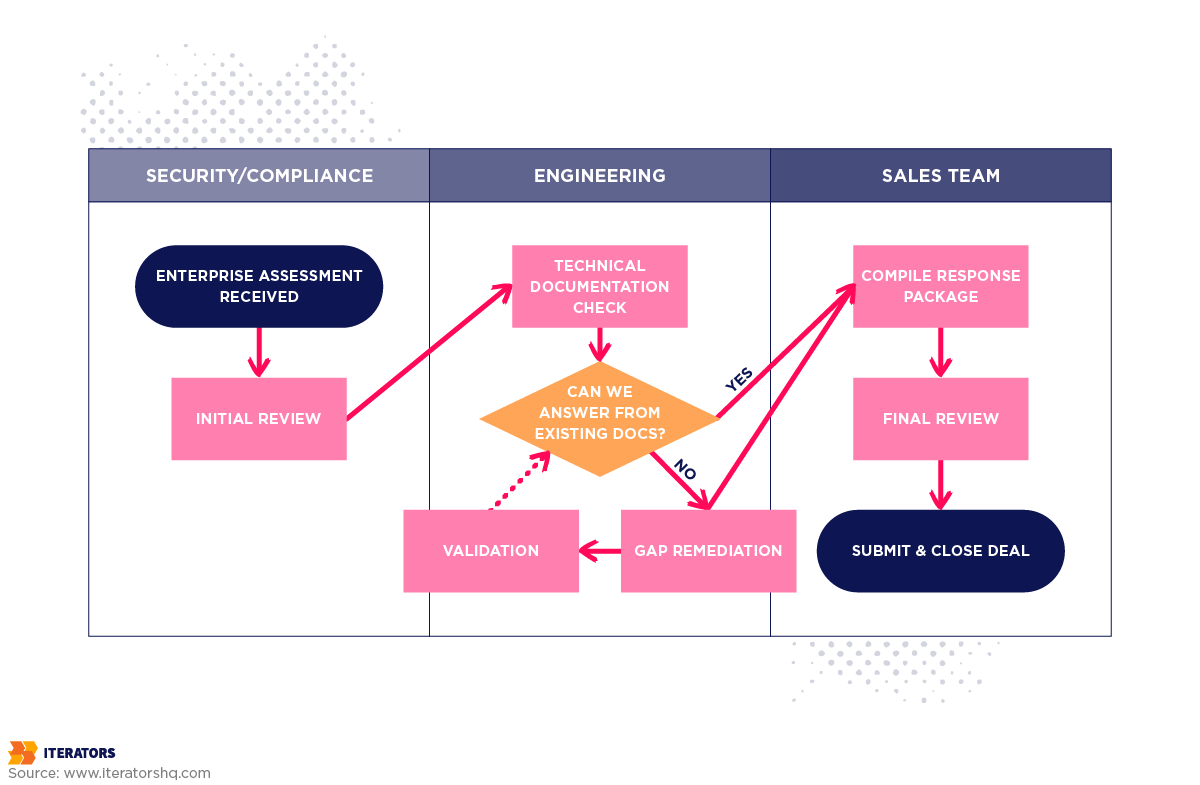
The “paper shield” is as important as the code shield in Enterprise Vendor Assessment contexts. Enterprise Vendor Assessments are document-heavy, and the quality of documentation signals the quality of your engineering.
The Self-Service Trust Center
Forward-thinking companies are moving away from emailing ZIP files of PDFs for every Enterprise Vendor Assessment. They use Trust Centers—public or gated web portals where customers can self-serve security artifacts.
Essential components for Enterprise Vendor Assessment acceleration:
- SOC 2 / ISO 27001 reports (watermarked, NDA-gated)
- Penetration test summaries (never the full report with exploit details)
- Real-time uptime status
- Subprocessor lists (who you use to process data)
- Security FAQs pre-answering common questionnaire items
Impact: This dramatically reduces Enterprise Vendor Assessment sales cycle friction. Your salesperson can send a link to the Trust Center instead of engaging legal and security for every request.
The Data Flow Diagram (DFD)
A high-quality DFD is the single most valuable artifact for security architects during Enterprise Vendor Assessments.
Requirements for Enterprise Vendor Assessment purposes:
- Show all entry and exit points
- Mark trust boundaries (Public Internet vs. DMZ vs. Private Subnet)
- Label data flows with protocols and ports (HTTPS/443)
- Indicate data stores and encryption status
Pro tip: Maintain a sanitized version (no internal IP addresses or secrets) specifically for sharing during Enterprise Vendor Assessments.
The “Golden” Questionnaire
Do not answer custom Enterprise Vendor Assessment questionnaires manually for every prospect.
Strategy for efficient Enterprise Vendor Assessment responses:
- Create a “Golden Response” set based on the SIG Core or CAIQ questionnaire
- When a prospect sends a custom Enterprise Vendor Assessment spreadsheet, reply: “We maintain a standard SIG/CAIQ which covers these controls. Will your team accept this format to expedite the review?”
- If they refuse, use AI-based questionnaire response tools (like HyperComply or Conveyor) to map your golden answers to their custom questions
This approach can reduce Enterprise Vendor Assessment turnaround time from weeks to days.
The 90-Day Roadmap: From Startup to Enterprise Vendor Assessment-Ready
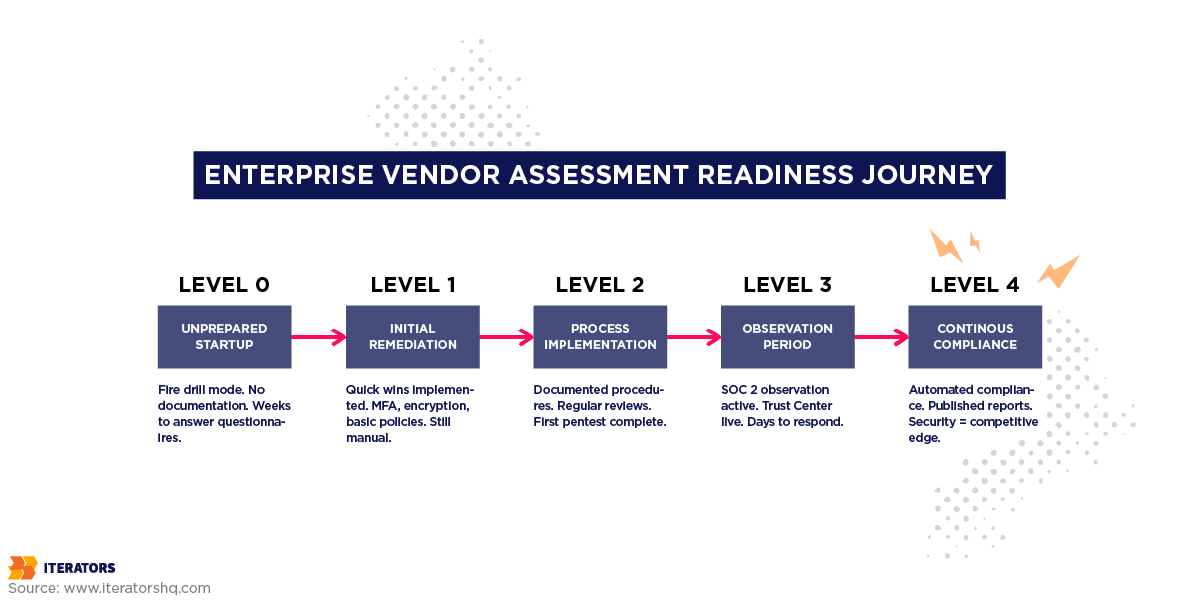
Transforming from a “move fast” startup to an “Enterprise Vendor Assessment-ready” vendor requires a deliberate operational sprint, similar to what we described in our guide on building the dream team.
Phase 1: Assessment and Gap Analysis (Days 1-30)
Week 1-2: Inventory
- Map all assets, vendors, and data flows
- Document your current architecture
- Identify who has access to what
Week 3-4: Framework Selection
- Choose SOC 2 vs. ISO 27001 based on target market
- Run a readiness scan using compliance automation tools
- Identify the biggest gaps (unencrypted databases, missing MFA, open security groups)
Deliverables:
- Asset inventory
- Gap analysis report
- Prioritized remediation plan
Phase 2: Remediation and Implementation (Days 31-60)
Week 5-6: Quick Wins
- Enable database encryption
- Implement MFA for all staff
- Configure centralized logging
- Tighten firewall rules
Week 7-8: Process Implementation
- Draft core policies (Acceptable Use, Access Control, Incident Response)
- Implement access review procedures
- Begin performing daily/weekly security tasks
- Commission third-party penetration test
Deliverables:
- Encrypted infrastructure
- Security policies
- Pentest report
Phase 3: The Observation Period (Days 61-90+)
Week 9-12: Operational Excellence
- Begin SOC 2 Type II observation window
- Operate controls consistently without exception
- Train sales team on security messaging
- Build Trust Center
- Conduct mock Enterprise Vendor Assessment with external consultant
Deliverables:
- Evidence of control operation
- Trust Center launch
- Sales enablement materials
Month 4-6: Audit and Certification
- Complete SOC 2 Type II audit
- Receive report
- Publish to Trust Center
- Begin using in Enterprise Vendor Assessment sales process
Common Failure Points (and How to Avoid Them)

Even with good intentions, startups make predictable mistakes during Enterprise Vendor Assessment initiatives, similar to the business logic flaws we’ve written about.
Mistake 1: Treating Compliance as a Checkbox
The trap: Viewing SOC 2 as something you “get” once and forget about.
Reality: Compliance is operational. Controls must be performed consistently. A single missed access review or unpatched server can result in a qualified audit opinion that will be discovered in future Enterprise Vendor Assessments.
Solution: Treat compliance as a daily operational metric, not an annual event. Use automation to enforce controls and alert when they drift.
Mistake 2: Over-Promising SLAs
The trap: Agreeing to aggressive SLAs (like 99.99% uptime or zero data loss) to win Enterprise Vendor Assessment negotiations.
Reality: If your architecture cannot support these commitments, you’re creating legal liability.
Solution: Be honest about current capabilities during Enterprise Vendor Assessments. Offer roadmap commitments for future improvements. Enterprises respect honesty more than false promises.
Mistake 3: Ignoring Documentation
The trap: Building great security architecture but failing to document it for Enterprise Vendor Assessment purposes.
Reality: If you cannot prove your security posture during an Enterprise Vendor Assessment, it doesn’t exist. Auditors and customers need evidence.
Solution: Treat documentation as a first-class product deliverable, as we emphasize in our guide on software documentation. Assign ownership. Review quarterly.
Mistake 4: Siloing Security
The trap: Making security “the CISO’s problem” instead of an engineering responsibility.
Reality: Security architecture is inseparable from product architecture. It cannot be bolted on at the end—a lesson that’s particularly relevant for tech infrastructure handovers.
Solution: Embed security in design reviews. Train developers on secure coding. Make security a shared responsibility.
Building Security as a Competitive Advantage in Enterprise Vendor Assessments

Here’s the counterintuitive truth: security compliance is not just a cost center—it’s a revenue accelerator in Enterprise Vendor Assessments.
When you can instantly produce a clean SOC 2 report, a comprehensive Data Flow Diagram, and a transparent SBOM during an Enterprise Vendor Assessment, the conversation shifts from “Is this risky?” to “When can we start?”
Your competitors are still scrambling to answer basic security questions in their Enterprise Vendor Assessments. You’re already moving to contract negotiation.
The requirements imposed by enterprise procurement—isolation, observability, resilience, strict access control—are largely synonymous with the requirements for a high-quality, scalable distributed system, following principles from enterprise security architecture.
By architecting for these constraints proactively, you build systems that are:
- Easier to debug (comprehensive logging)
- Safer to operate (least privilege access)
- More resilient to failure (disaster recovery testing)
- Faster to audit (self-documenting architecture)
In a market where trust is currency, the ability to demonstrate mature security posture during Enterprise Vendor Assessments becomes a powerful differentiator.
Your Next Steps to Enterprise Vendor Assessment Readiness

If you’re reading this and thinking “we need to get Enterprise Vendor Assessment-ready,” here’s your action plan:
This Week:
- Run a gap assessment against SOC 2 requirements
- Document your current architecture (even if it’s embarrassing)
- Enable MFA for all staff accounts
This Month:
- Choose a compliance framework (SOC 2 or ISO 27001)
- Implement SSO/SCIM if you haven’t already
- Commission a penetration test
- Draft your core security policies
This Quarter:
- Complete initial remediation work
- Begin SOC 2 observation period
- Build your Trust Center
- Train your sales team on security messaging
This Year:
- Complete SOC 2 Type II audit
- Publish your first compliance report
- Win your first enterprise deal with security as a competitive advantage
- Streamline your Enterprise Vendor Assessment response process
The journey to Enterprise Vendor Assessment readiness is rigorous, but the view from the summit—access to the world’s largest customers—is worth the climb.
The companies that treat security architecture as a strategic asset, not a compliance burden, are the ones that win enterprise deals while their competitors are still filling out Enterprise Vendor Assessment questionnaires.
Your product solves real problems. Make sure your architecture proves you can be trusted to solve them securely—and that you can demonstrate that trust quickly and convincingly during every Enterprise Vendor Assessment.
Frequently Asked Questions About Enterprise Vendor Assessments
How long does it really take to prepare for Enterprise Vendor Assessments and get SOC 2 certified?
The realistic timeline is 4-6 months minimum. You need at least 3 months of observation period for a Type II report, plus 1-2 months for remediation and 1 month for the actual audit. Companies claiming “SOC 2 in 30 days” are selling Type I reports, which prove you designed controls but not that they work. For Enterprise Vendor Assessment purposes, Type II is what matters—and it’s a marathon, not a sprint.
Can we pass Enterprise Vendor Assessments without SOC 2?
Technically yes, but it’s much harder. You’ll need to answer detailed questionnaires for every prospect and provide custom evidence packages. SOC 2 is essentially a “pre-answered questionnaire” that satisfies most Enterprise Vendor Assessment requirements. The ROI typically justifies the $20,000-$50,000 investment once you’re pursuing deals over $100,000.
What if we fail an Enterprise Vendor Assessment?
Most Enterprise Vendor Assessments don’t result in binary pass/fail. Instead, they identify “findings” or gaps. You’ll typically get a chance to remediate issues or accept them as “residual risks” with compensating controls. The key is being transparent about limitations and having a roadmap for improvement. Many enterprises will accept “we don’t have this today, but it’s on our roadmap for Q3” if you can demonstrate maturity in other areas.
Do we need to build everything in-house or can we rely on cloud provider security for Enterprise Vendor Assessments?
You can absolutely leverage your cloud provider’s security certifications (AWS, Azure, and GCP all have SOC 2, ISO 27001, and more) for Enterprise Vendor Assessment responses. This is called “inheritance.” For example, you can reference Azure Security Architecture or Google Cloud Security Command Center documentation in your assessments. However, you’re still responsible for how you configure those services. A misconfigured S3 bucket is your fault, not AWS’s, and will be a red flag in any Enterprise Vendor Assessment.
How much does Enterprise Vendor Assessment readiness actually cost?
Budget $50,000-$150,000 for your first year, including:
- SOC 2 audit: $20,000-$50,000
- Penetration testing: $10,000-$30,000
- Compliance automation platform: $10,000-$30,000/year
- Security tooling (SIEM, vulnerability scanning): $10,000-$20,000/year
- Engineering time: Varies widely, but expect 1-2 engineers spending 20-30% of their time on security for 3-6 months
The investment pays for itself quickly once you start winning enterprise deals that previously took months to close due to Enterprise Vendor Assessment delays.
How often do enterprise customers re-assess vendors?
Most enterprises require annual re-assessments, which is why SOC 2 reports are issued annually. Some also use continuous monitoring services (like SecurityScorecard) that scan your public-facing infrastructure daily. The good news: once you’ve built the foundation for passing Enterprise Vendor Assessments, annual re-assessments are much lighter lifts—often just providing updated SOC 2 reports and answering a few targeted follow-up questions.
Can we use open-source tools or do we need expensive enterprise security products for Enterprise Vendor Assessment readiness?
Many excellent security tools are open-source or have generous free tiers. For example, you can build comprehensive logging with the ELK stack, implement SCIM with open-source libraries, and generate SBOMs with free tools like Syft. The key is implementation quality, not tool cost. That said, compliance automation platforms (Vanta, Drata) can dramatically reduce operational burden and are often worth the investment—they essentially become your “always-on” Enterprise Vendor Assessment readiness system.
What’s the difference between an Enterprise Vendor Assessment and a security audit?
An Enterprise Vendor Assessment is typically a questionnaire-based evaluation that a prospective customer performs before signing a contract. A security audit (like SOC 2) is a formal examination by an independent third party that results in an official report. Think of it this way: the SOC 2 audit is the “test,” and the Enterprise Vendor Assessment is showing your report card to potential customers. Having a clean SOC 2 report dramatically accelerates Enterprise Vendor Assessment processes because it pre-answers most questions with audited evidence.
Should we pursue SOC 2 or ISO 27001 first for our Enterprise Vendor Assessment strategy?
For most U.S.-based B2B SaaS startups, start with SOC 2—it’s what North American enterprises expect during their Enterprise Vendor Assessment process. Pursue ISO 27001 when you’re expanding internationally, particularly to Europe and Asia, where it’s often the primary requirement. Some companies eventually maintain both certifications to address different market requirements, but SOC 2 should be your initial focus if you’re primarily targeting U.S. enterprises.
How do we handle Enterprise Vendor Assessments when we’re using multiple cloud providers or third-party services?
This is where your subprocessor list becomes critical. You need to maintain a current inventory of every third-party service that processes customer data (cloud hosting, analytics, support tools, etc.). During Enterprise Vendor Assessments, you’ll need to demonstrate that:
- Each subprocessor has appropriate security certifications (ideally SOC 2 or ISO 27001)
- You have data processing agreements (DPAs) in place with each vendor
- You’ve performed due diligence on their security practices
- You have a process for notifying customers when subprocessors change
Many enterprises want the right to review or approve subprocessor additions, so build this transparency into your Trust Center from the start. For guidance on evaluating your own vendors, you can reference resources on vendor risk assessment processes and third-party risk management best practices.
Ready to build an Enterprise Vendor Assessment-ready architecture but not sure where to start? At Iterators, we help B2B SaaS companies architect secure, compliant platforms that accelerate enterprise sales cycles. Our team has guided dozens of startups through their first SOC 2 audits and enterprise customer onboarding processes. Contact us to learn how we can help you turn security compliance from a bottleneck into your competitive advantage.
